NOTE: In this case, the client anyconnect configuration will show that only 10.10.10.0/24 as the secured route. As piotr pointed out, encrypt everything from client to ASA, and have the ASA query the web server on behalf of the client and reply back to the SSL VPN client (diagram attached). Ip local pool AnyConnect-Pool 192.168.50.1-192.168.50.10 mask 255.255.255.0 group-policy AnyConnect-GP internal group-policy AnyConnect-GP attributes vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified split-tunnel-network-list value AnyConnect-ACL tunnel-group AnyConnect-TG type remote-access tunnel-group AnyConnect-TG general.
- Cisco Anyconnect Vpn Protocol
- Anyconnect Ssl Vpn Client
- Cisco Anyconnect Ssl Vpn Client Download
- Anyconnect Ssl Client
Overview
ASA: 8.3+ (Written/Tested on 9.0)
Authentication: Local (Local ASA User Database)
Type: Split-tunnel OR Non split-tunnel
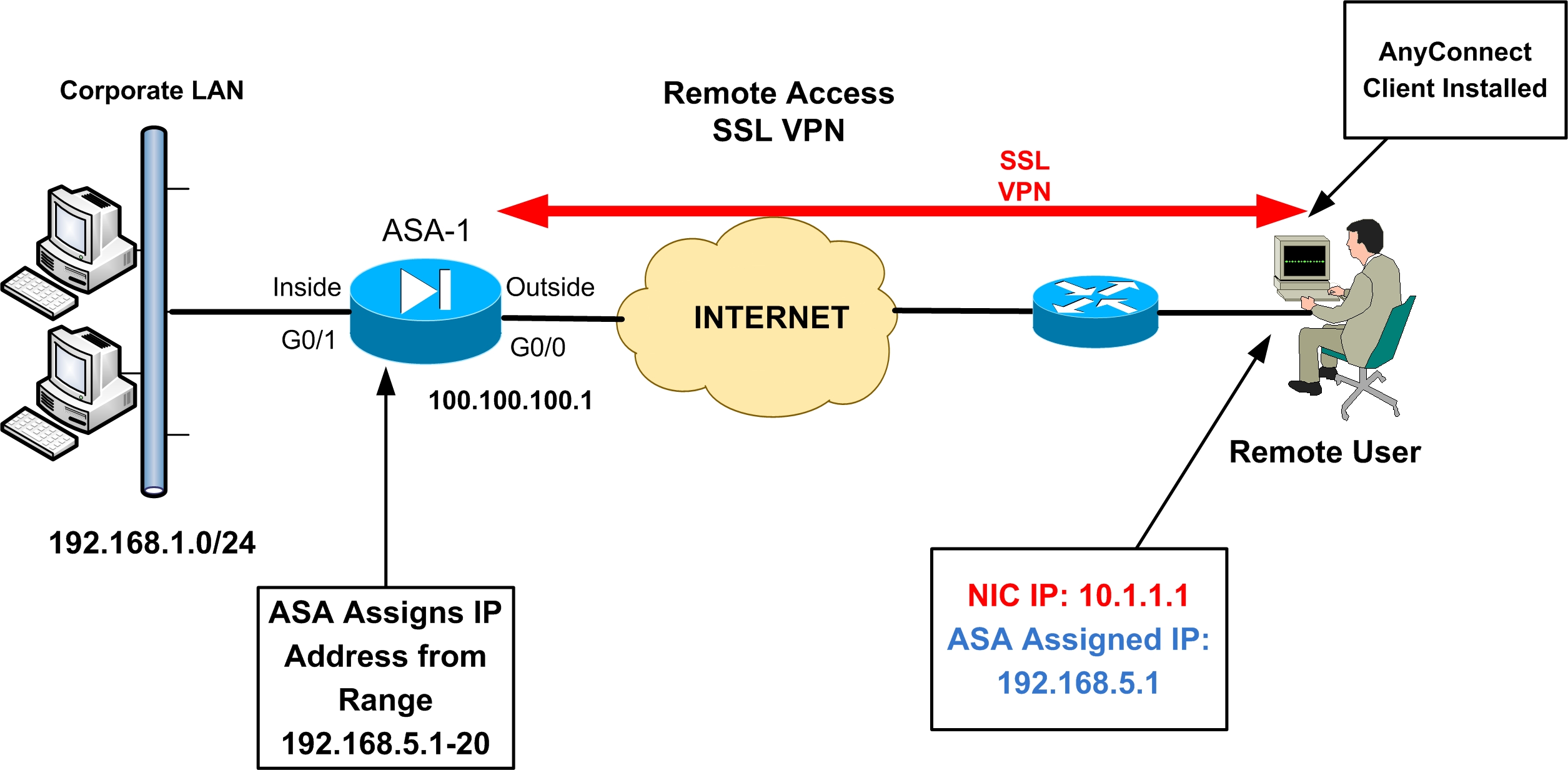
The below configurations will work with 8.3+, but was written and tested with 9.0. When setting up a Anyconnect VPN tunnel, you can push all traffic from the client over the VPN (Tunnel all) or you can use a split tunnel to only push traffic destined for selected subnets over the VPN tunnel. In laymen terms, the clients internet traffic originates from their ISP in a split tunnel, and it originates from the ASA when using tunnel all. The below configuration examples assume you have a basic setup equivalent to running factory-default and are setup to authenticate locally to the ASA. I will give examples of each configuration below.
Network Diagram
The ASA has a command that gives an overview of how to configure an Anyconnect SSL VPN, which in global configuration mode is vpnsetup ssl-remote-access steps. Here are the results of that command:
There are a few important things to note from Cisco’s directions:
- They are using the default names for configuring the group policy and tunnel groups, which will throw a warning that they already exist since they’re defaults
- The directions do not specify that you MUST attach the VPN Address pool to the tunnel group, which is necessary for it to work!
- They do not include how to create a split tunnel or a tunnel all to allow internet from the Anyconnect client.
- They are using outdated “svc” commands, which were replaced with “anyconnect”.
Cisco Anyconnect Vpn Protocol
With that said, let’s move on to the configurations!
Anyconnect Configuration 1: Tunnel All
Anyconnect Configuration 2: Split Tunnel
Anyconnect Ssl Vpn Client
Testing the Configuration
Open a web browser, connect to your ASA (https://vpn.domain.com OR https://172.31.100.1), and you’ll be prompted to login. You can login with the user account you’ve created in the configuration above. The Anyconnect client will automatically install, if it fails you may need to download and manually install it. Once installed, you can connect to your ASA by the outside interface (vpn.domain.com OR 172.31.100.1) and authenticate with the user you’ve created.
Cisco Anyconnect Ssl Vpn Client Download
Additional Notes
Anyconnect Ssl Client
You may wish to use a 3rd party SSL certificates (ie: Verisign, Thawte, Godaddy, etc) so end users do not get prompted about certificate warnings. Cisco ASA’s will regenerate it’s certificate upon reboot, and due to this you should create a self signed certificate whenever you cannot use a 3rd party. You can create the self signed certificate as follows:
