Analytics cookies. We use analytics cookies to understand how you use our websites so we can make them better, e.g. They're used to gather information about the pages you visit and how many clicks you need to accomplish a task. Content Security Policy Cheat Sheet¶ Introduction¶. This article brings forth a way to integrate the defense in depth concept to the client-side of web applications. By injecting the Content-Security-Policy (CSP) headers from the server, the browser is aware and capable of protecting the user from dynamic calls that will load content into the page currently being visited. XSS Filter Evasion Payloads These payloads come from the OWASP XSS Filter Evasion Cheat Sheet The payloads contained here can be loaded into a dynamic testing tool such as Burp or OWASP ZAP Check the OWASP wiki if you want to know the intended bypass method for each payload.
Last revision (mm/dd/yy): 07/4/2018 This cheat sheet lists a series of XSS attacks that can be used to bypass certain XSS defensive filters. Please note that input filtering is an incomplete defense for XSS which these tests can be used to illustrate. Basic XSS Test Without Filter Evasion This is a normal XSS JavaScript injection, and most likely to get caught but I suggest trying it first (the quotes are not required in any modern browser so they are omitted here): XSS Locator (Polygot) The following is a 'polygot test XSS payload.' javascript:/*--></title></style></textarea></script></xmp><svg/onload='+/'/+/onmouseover=1/+/[*/[]/+alert(1)//'> Image XSS using the JavaScript directive Image XSS using the JavaScript directive (IE7.0 doesn't support the JavaScript directive in context of an image, but it does in other contexts, but the following show the principles that would work in other tags as well: No quotes and no semicolon Case insensitive XSS attack vector HTML entities Malformed A tags <! <!ArchivesApproximately 1 year ago today, Tim Tomes and I did a presentation on Volume Shadow Copies (VSC) at Hack3rCon II. Hack3rCon^3 just wrapped up, and I’ve officially been shamed into finally publishing the details of the research. Many of the faithful PDC readers will know most of these details, as some of them were included as pieces to posts on other topics, but I will try to provide a little something new. Volume Shadow Copies The Volume Shadow Copy Service (VSS) maintains copies of every 16k block that is changed on an NTFS disk. Then at certain times it packages up all those 16k blocks and puts them up into a Volume Shadow Copy (VSC).
An Introduction to Content Security PolicyThe web’s security model is rooted in the same origin policy. Code from should only have access to data, and should certainly never be allowed access. Each origin is kept isolated from the rest of the web, giving developers a safe sandbox in which to build and play. In theory, this is perfectly brilliant. In practice, attackers have found clever ways to subvert the system. Cross-site scripting (XSS) attacks, for example, bypass the same origin policy by tricking a site into delivering malicious code along with the intended content.Paper: Kr3w's Cross-Site Scripting TutorialPart I. What is XSS (Cross-Site Scripting)? XSS, short for what is known as Cross-Site Scripting is the process of injecting JavaScript (mainly) and also HTML into a webpage for important feedback. This feedback may contain many things; one, most commonly being the user's cookie. Now, for everybody reading this, I assume that you know what a cookie is and how it is used on webpage, but if not, I will explain it anyways.
BlogsDEP (Data Execution Prevention) and ASLR (Address Space Layout Randomization) have proven themselves to be important and effective countermeasures against the types of exploits that we see in the wild today. Of course, any useful mitigation technology will attract scrutiny, and over the past year there has been an increasing amount of research and discussion on the subject of bypassing DEP and ASLR [1,2]. In this blog post we wanted to spend some time discussing the effectiveness of these mitigations by providing some context for the bypass techniques that have been outlined in attack research. The key points that should be taken away from this blog post are: DEP and ASLR are designed to increase an attacker's exploit development costs and decrease their return on investment.The combination of DEP and ASLR is very effective at breaking the types of exploits we see in the wild today, but there are circumstances where they can both be bypassed.
DOM based XSS Prevention Cheat SheetLast revision (mm/dd/yy): 11/25/2017 In order to understand DOM based XSS, one needs to see the fundamental difference between Reflected and Stored XSS when compared to DOM based XSS. The primary difference is where the attack is injected into the application. Reflected and Stored XSS are server side injection issues while DOM based XSS is a client (browser) side injection issue. All of this code originates on the server, which means it is the application owner's responsibility to make it safe from XSS, regardless of the type of XSS flaw it is.Maltego Part I - Intro and Personal ReconBy Chris Gates, CISSP, GCIH, C|EH, CPTS According to their web site, “Paterva invents and sells unique data manipulation software. Paterva is headed by Roelof Temmingh who is leading a light and lethal team of talented software developers.” On May 6 2008, they released a new version of a very kewl tool named Maltego. “Maltego, is an open source intelligence and forensics application. It allows for the mining and gathering of information as well as the representation of this information in a meaningful way.
.Net HTML sanitizer (“The library is unit tested with the OWASP XSS Filter Evasion Cheat Sheet“) OWASP Java HTML Sanitizer; Python Bleach; For an in-depth and updated list of practices, check out The Open Web Application Security Project (OWASP). Cross-site scripting (XSS) is a vulnerability that allows an attacker to inject code (usually HTML or JavaScript) into a website. When a victim views an infected page, the injected code runs in their browser.
Web design trends we love – WeavoraI think most of you will agree that when it comes to websites, design really matters! Sometimes that’s what the whole project is about. The time has passed when visual representation bore less importance than content. “Life moves pretty fast; if you don’t stop and look around once in a while, you could miss it”.XSS - Stealing Cookies 101Stealing cookies is easy. Never trust a client to be who you think it is. Just because it was trusted a few seconds ago, doesn't mean it will be in a few seconds, ESPECIALLY if a cookie is all you use to identify a client. A recent LiveJournal hack has brought this to light again. Back when MySpace was hacked in October it reminded us that we must be vigilant in filtering text which users post because a hacker could smuggle in some javascript code to maliciously use the site from the browsers of authenticated users. By stealing a users cookies as the LiveJournal hack did, you don't even have to cary out the attack in the users browser; you can do it elsewhere.
Owasp Xss Filter Evasion Cheat Sheet Download
Boffins ‘crack’ HTTPS encryption in Lucky Thirteen attackThe security of online transactions is again in the spotlight as a pair of UK cryptographers take aim at TLS. TLS, or Transport Layer Security, is the successor to SSL, or Secure Sockets Layer. It's the system that puts the S into HTTPS (that's the padlock you see on secure websites), and provides the security for many other protocols, too. Like 2011's infamous BEAST attack, it has a groovy name: Lucky Thirteen. The name comes from the fact that encrypted TLS packets have thirteen header bytes that are consumed in one of the cryptographic calculations on which TLS relies.
Related:Resolution

Overview
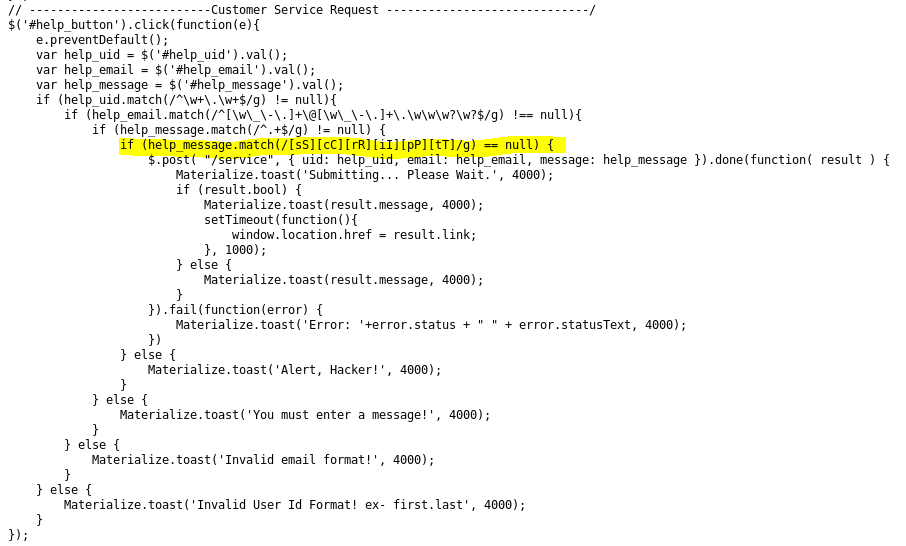
This document describes a test to generate a 'Generic Cross Site Scripting' event in the threat log.
Details
- Create a policy that allows the web-browsing and SSL applications.
- Apply the DEFAULT Vulnerability Protection security profile associated with the policy.
- Go to any web page and look for an entry box that allows any typed entries.
- Enter the following text into the entry box: <script>alert(XSS Test)</script>
For example, the following image shows the amazon.com website with the given text entered into the 'Search' box:
In the example above, when Enter is pressed after entering the text, the browser was busy for a while before displaying a message that the connection was reset. - Go to Monitor > Threat on the PAN-OS Web GUI, and an alert appears in the threat log. The action shows that a TCP RESET was sent to the server.
Xss Injection Cheat Sheet
The global counters can also be viewed to confirm that the firewall has sent TCP reset packets:
> show counter global | match RST
flow_action_close 4 0 drop flow pktproc TCP sessions closed via injecting RST
Owasp Xss Filter Evasion Cheat Sheet Free
See Also
For additional examples: XSS Filter Evasion Cheat Sheet - OWASP
Rsnake Xss Cheat Sheet

owner: skrall

Attachments
